Welcome, curious minds, to this fascinating exploration of the world of computer networking! Join me as we embark on a journey through the digital highways and byways, uncovering the mysteries and marvels of network architecture.
Unveiling the Layers of Knowledge
Book Suggestions:
For those eager to delve into the depths of networking, I found the following books:
| Level | Book Name | Approx. Number of Pages |
| Beginner | "Networking For Dummies" by Doug Lowe | 456 |
| Intermediate | "Computer Networking: A Top-Down Approach" by James F. Kurose and Keith W. Ross | 864 |
| Intermediate | "TCP/IP Illustrated, Volume 1: The Protocols" by W. Richard Stevens | 832 |
| Intermediate | "Computer Networks: A Systems Approach" by Larry L. Peterson and Bruce S. Davie | 832 |
| Intermediate | "Network Warrior" by Gary A. Donahue | 792 |
| Intermediate | "TCP/IP Guide: A Comprehensive, Illustrated Internet Protocols Reference" by Charles M. Kozierok | 1648 |
| Intermediate | "Data and Computer Communications" by William Stallings | 912 |
| Intermediate | "UNIX Network Programming, Volume 1: The Sockets Networking API" by W. Richard Stevens | 1008 |
| Advanced | "Internetworking with TCP/IP Volume One: Principles, Protocols, and Architecture" by Douglas E. Comer | 840 |
| Advanced | "Computer Networking: Principles, Protocols, and Practice" by Olivier Bonaventure | 656 |
| Advanced | "TCP/IP Network Administration" by Craig Hunt | 928 |
| Advanced | "The TCP/IP Guide: A Comprehensive, Illustrated Internet Protocols Reference" by Charles M. Kozierok | 1680 |
| Advanced | "UNIX Network Programming, Volume 2: Interprocess Communications" by W. Richard Stevens | 1072 |
| Advanced | "Computer Networking Problems and Solutions: An innovative approach to building resilient, modern networks" by Russ White and Ethan Banks | 562 |
| Advanced | "Network Security Essentials: Applications and Standards" by William Stallings | 560 |
| Expert | "TCP/IP Illustrated, Volume 2: The Implementation" by Gary R. Wright and W. Richard Stevens | 1200 |
| Expert | "Advanced Programming in the UNIX Environment" by W. Richard Stevens | 960 |
| Expert | "Cisco Networking Essentials" by Troy McMillan | 368 |
| Expert | "CCNA Routing and Switching Portable Command Guide" by Scott Empson | 400 |
| Expert | "CCNA Security 210-260 Official Cert Guide" by Omar Santos, John Stuppi | 720 |
| Expert | "CCNP Routing and Switching ROUTE 300-101 Official Cert Guide" by Kevin Wallace, Wendell Odom | 1024 |
| Expert | "CCIE Routing and Switching v5.0 Official Cert Guide, Volume 1" by Narbik Kocharians, Peter Paluch, Wendell Odom | 936 |
| Expert | "Wireshark 101: Essential Skills for Network Analysis" by Laura Chappell | 376 |
| Expert | "Practical Packet Analysis: Using Wireshark to Solve Real-World Network Problems" by Chris Sanders | 448 |
Diving into Topics:
Let's dive deep into the core components of network architecture:
Topology Tales:
Imagine the network as a bustling city, with its streets and alleys representing different topologies. From the straightforward bus topology to the star-studded glamour of the star topology, each layout has its own charm. But let's not forget the mesh topology, where connections intertwine like a complex web, ensuring redundancy and resilience.
Real-life example: Why did the topology throw a party? Because it wanted to see some star connections!
Protocols and Standards Safari:
Ah, protocols and standards, the backbone of network communication! TCP/IP, Ethernet, Wi-Fi – these are the languages spoken by devices as they exchange data packets across the digital landscape. It's like a global symphony, with each protocol playing its part in the grand orchestration of connectivity.
Real-life example: Why did the UDP packet go to therapy? Because it had trouble with its connections – it couldn't establish a reliable relationship!
Devices in the Digital Jungle:
Routers, switches, hubs – oh my! These devices are the gatekeepers of the network, directing traffic, filtering data, and ensuring smooth transmission. Think of them as the traffic cops of cyberspace, keeping the digital highways flowing smoothly.
Real-life example: Why was the router feeling down? Because it had too many packets to process – it was suffering from packet overload!
Navigating the Network Wilderness with a Tree Diagram
Network Architecture
Topology
Physical
Bus
Coaxial Cable
Linear Bus
Star
Centralized Star
Distributed Star
Ring
Token Ring
FDDI (Fiber Distributed Data Interface)
Mesh
Full Mesh
Partial Mesh
Hybrid
Star-Ring Hybrid
Star-Bus Hybrid
Logical
Ethernet
10BASE-T
100BASE-TX
1000BASE-T
10GBASE-T
Wi-Fi
IEEE 802.11a
IEEE 802.11b
IEEE 802.11g
IEEE 802.11n
IEEE 802.11ac
IEEE 802.11ax
- Protocols and Standards
TCP/IP
TCP
TCP Segmentation Offload (TSO)
TCP Fast Open (TFO)
TCP Keepalive
TCP Window Scaling
UDP
UDP Checksum
UDP Hole Punching
IP
IPv4
IPv4 Header
IPv4 Address Classes
IPv6
IPv6 Header
IPv6 Address Types
ICMP
ICMP Echo Request/Reply (Ping)
ICMP Time Exceeded
ICMP Destination Unreachable
ARP
ARP Request/Reply
ARP Cache Poisoning
Ethernet
IEEE 802.3
IEEE 802.3u
IEEE 802.3z
Ethernet Frame Format
Wi-Fi
IEEE 802.11
IEEE 802.11i
HTTP
HTTP Methods (GET, POST, PUT, DELETE)
HTTP Status Codes
DNS
DNS Resolution Process
DNS Record Types (A, AAAA, CNAME, MX, etc.)
DHCP
DHCP Discover/Offer/Request/Acknowledge
DHCP Lease Renewal
SNMP
SNMPv1, SNMPv2c, SNMPv3
SNMP MIB Structure
- Network Devices
Routers
Cisco ISR Routers
Cisco ASR Routers
Juniper MX Series Routers
Switches
Cisco Catalyst Switches
Cisco Nexus Switches
Juniper EX Series Switches
Hubs
- Hub vs. Switch
Modems
DSL Modems
Cable Modems
Firewalls
Next-Generation Firewalls (NGFW)
Intrusion Detection/Prevention Systems (IDS/IPS)
NICs
Ethernet NICs
Wireless NICs
- Addressing and Naming
IP Addresses
IPv4
IPv4 Subnetting
IPv4 Private vs. Public Addresses
IPv6
IPv6 Address Allocation
IPv6 Link-Local Addresses
MAC Addresses
MAC Address Format
MAC Address Resolution
Domain Names
Domain Name Structure
Domain Name Registrars
- Routing and Switching
Routing Protocols
OSPF
OSPF Hello Protocol
OSPF LSAs (Link State Advertisements)
BGP
BGP Peering
BGP Attributes
EIGRP
EIGRP Hello Protocol
EIGRP Metrics
Switching Techniques
Store-and-Forward
Cut-Through
Fragment-Free
VLANs
VLAN Trunking (802.1Q)
VLAN Tagging
- Security
Encryption
Symmetric Encryption
AES (Advanced Encryption Standard)
DES (Data Encryption Standard)
Asymmetric Encryption
RSA
ECC (Elliptic Curve Cryptography)
Authentication
RADIUS
RADIUS Authentication Process
RADIUS Accounting
TACACS+
- TACACS+ vs. RADIUS
Access Control Lists (ACLs)
Standard ACLs
Extended ACLs
- VPN (Virtual Private Network)
VPN Protocols (IPsec, SSL/TLS, PPTP, L2TP, OpenVPN)
VPN Tunneling
- Scalability and Performance
Load Balancing
- Load Balancer Algorithms (Round Robin, Least Connections, etc.)
Caching
Web Caching
DNS Caching
Compression
Data Compression Techniques
HTTP Compression
Bandwidth Management
Traffic Shaping
Rate Limiting
Quality of Service (QoS)
- QoS Models (Best-Effort, Integrated Services, Differentiated Services)
- Redundancy and High Availability
Redundant Power Supplies
Link Aggregation (EtherChannel)
HSRP/VRRP/GLBP
Failover Clustering
Server Failover
Network Failover
- Management and Monitoring
SNMP (Simple Network Management Protocol)
Management Information Base (MIB)
MIB Structure
MIB Objects
SNMPv3
SNMPv3 Authentication
SNMPv3 Encryption
Syslog
Syslog Levels
Syslog Servers
Network Monitoring Tools
Ping
Traceroute
NetFlow
Some acronyms
Let's explore the key acronyms that form the backbone of network architecture:
TCP/IP - Transmission Control Protocol/Internet Protocol
OSI - Open Systems Interconnection
LAN - Local Area Network
WAN - Wide Area Network
WLAN - Wireless Local Area Network
MAN - Metropolitan Area Network
VPN - Virtual Private Network
NAT - Network Address Translation
DHCP - Dynamic Host Configuration Protocol
DNS - Domain Name System
HTTP - Hypertext Transfer Protocol
HTTPS - Hypertext Transfer Protocol Secure
FTP - File Transfer Protocol
SMTP - Simple Mail Transfer Protocol
POP - Post Office Protocol
IMAP - Internet Message Access Protocol
ICMP - Internet Control Message Protocol
ARP - Address Resolution Protocol
VLAN - Virtual Local Area Network
MAC - Media Access Control
PPP - Point-to-Point Protocol
PPPoE - Point-to-Point Protocol over Ethernet
DSL - Digital Subscriber Line
VoIP - Voice over Internet Protocol
QoS - Quality of Service
MPLS - Multiprotocol Label Switching
BGP - Border Gateway Protocol
OSPF - Open Shortest Path First
EIGRP - Enhanced Interior Gateway Routing Protocol
RIP - Routing Information Protocol
SNMP - Simple Network Management Protocol
SSH - Secure Shell
SSL - Secure Sockets Layer
TLS - Transport Layer Security
IPsec - Internet Protocol Security
WPA - Wi-Fi Protected Access
WEP - Wired Equivalent Privacy
WPA2 - Wi-Fi Protected Access 2
IEEE - Institute of Electrical and Electronics Engineers
IEEE 802.11 - Wireless LAN standards
IEEE 802.3 - Ethernet standards
TCP - Transmission Control Protocol
UDP - User Datagram Protocol
IP - Internet Protocol
IPv4 - Internet Protocol version 4
IPv6 - Internet Protocol version 6
ICMPv6 - Internet Control Message Protocol version 6
FTPS - FTP Secure
SFTP - SSH File Transfer Protocol
CIDR - Classless Inter-Domain Routing
NAT64 - Network Address Translation IPv6 to IPv4
DHCPv6 - Dynamic Host Configuration Protocol version 6
PPTP - Point-to-Point Tunneling Protocol
L2TP - Layer 2 Tunneling Protocol
GRE - Generic Routing Encapsulation
STP - Spanning Tree Protocol
RSTP - Rapid Spanning Tree Protocol
MSTP - Multiple Spanning Tree Protocol
VTP - VLAN Trunking Protocol
ISDN - Integrated Services Digital Network
ATM - Asynchronous Transfer Mode
FDDI - Fiber Distributed Data Interface
SDN - Software-Defined Networking
CDN - Content Delivery Network
HTTP/2 - Hypertext Transfer Protocol version 2
SNMPv3 - Simple Network Management Protocol version 3
IPv6 ND - IPv6 Neighbor Discovery
BFD - Bidirectional Forwarding Detection
LACP - Link Aggregation Control Protocol
LLDP - Link Layer Discovery Protocol
HSRP - Hot Standby Router Protocol
VRRP - Virtual Router Redundancy Protocol
HSRP - Hot Standby Router Protocol
QoS - Quality of Service
VoLTE - Voice over LTE
DMZ - Demilitarized Zone
IoT - Internet of Things
M2M - Machine to Machine
PoE - Power over Ethernet
DNSSEC - Domain Name System Security Extensions
DDoS - Distributed Denial of Service
SSO - Single Sign-On
RADIUS - Remote Authentication Dial-In User Service
TACACS+ - Terminal Access Controller Access-Control System Plus
NTP - Network Time Protocol
GRE - Generic Routing Encapsulation
VXLAN - Virtual Extensible LAN
MLAG - Multi-Chassis Link Aggregation
NFV - Network Function Virtualization
SD-WAN - Software-Defined Wide Area Network
VRF - Virtual Routing and Forwarding
SNMPv2c - Simple Network Management Protocol version 2c
PIM - Protocol Independent Multicast
IGMP - Internet Group Management Protocol
VLSM - Variable Length Subnet Masking
PoE+ - Power over Ethernet Plus
SFTP - Secure File Transfer Protocol
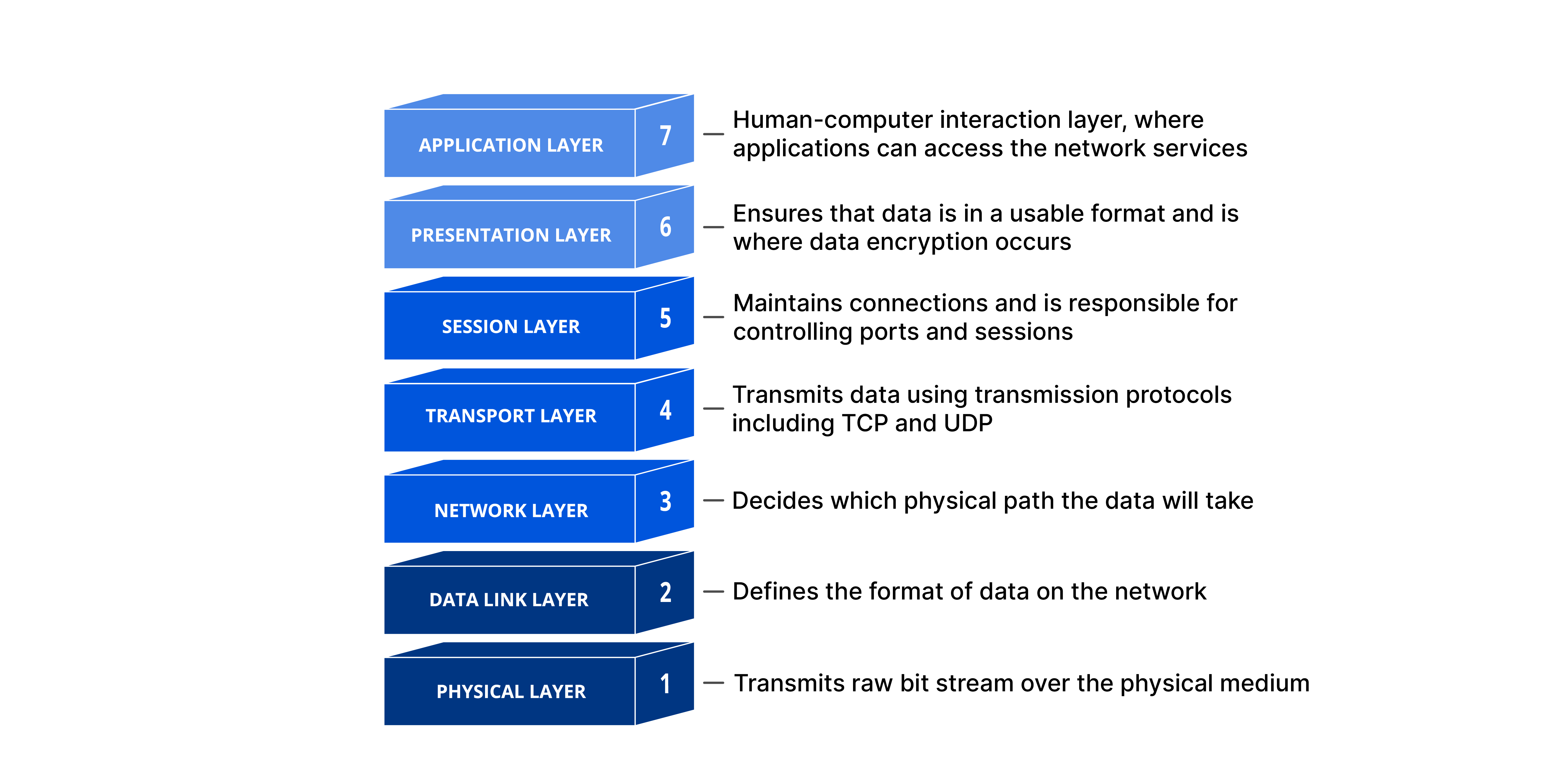
OSI Model
The intent of the OSI model is to provide a framework for networking that ensures compatibility in the network hardware and software and to accelerate the development of new networking technologies.
Conclusion: Embracing the Network Adventure
As we conclude our curious journey through the realms of networking, I hope you've gained a newfound appreciation for the intricacies of this digital domain. Whether you're a seasoned explorer or a curious novice, there's always something new to discover in the world of network architecture.
So, dear reader, continue to journey forth with curiosity as your guide, and may your network connections be strong, and your packets always reach their destination!
Stay curious, stay connected!